Choose the right entitlements
In Google Cloud's Privileged Access Management (PAM), entitlements are the fundamental building blocks that define and control how users can request and gain temporary access to sensitive resources. Think of them as pre-defined rules that govern who can ask for what kind of privileged access, for how long, and whether that request needs approval.
Know more about PAM entitlements
-
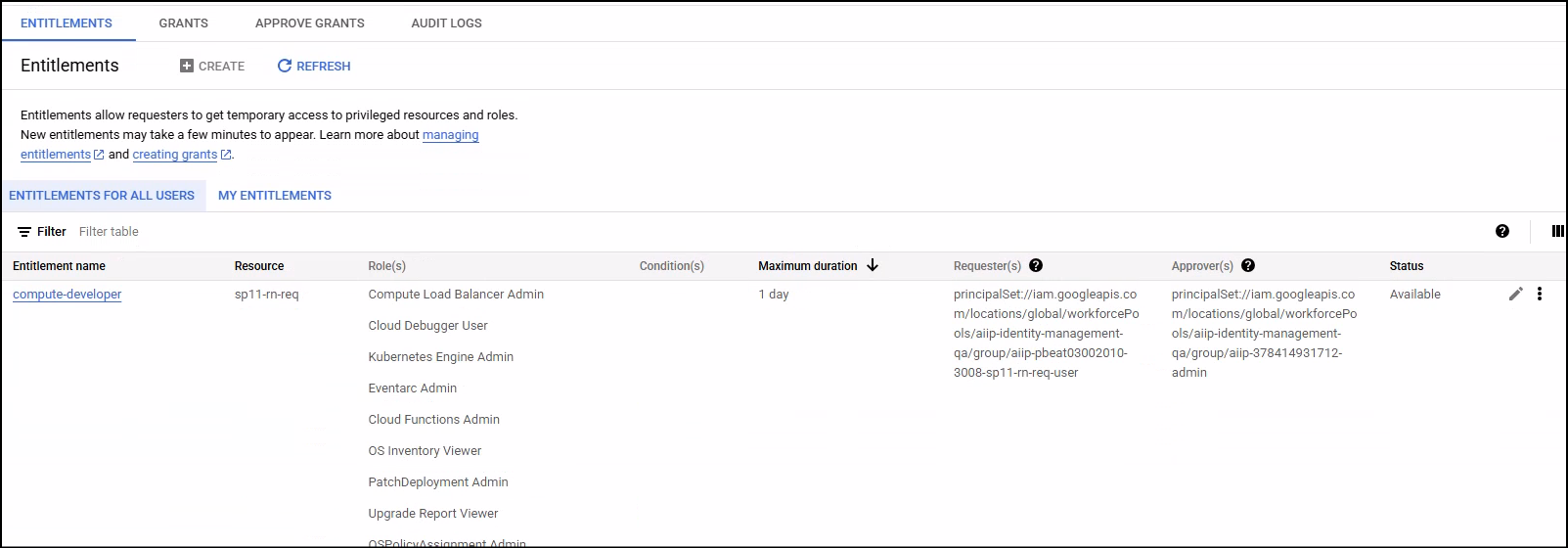
Definition of Privileged Access: An entitlement specifies a set of IAM roles that will be temporarily granted upon a successful request. These roles can apply to a specific organization, folder, or project. IAM Conditions can also be applied to these roles for more granular control, allowing for highly specific access (e.g., "only allow access to Storage buckets with a specific tag").
-
Maximum request duration: Each entitlement defines the maximum amount of time for which a grant can be requested. This duration is crucial for enforcing time-bound access. Depending on the access level, the max duration is set for AIIP Projects.
-
Eligible requesters: This is a list of users/groups that are allowed to request grants against this entitlement.
-
Approval workflow: Entitlements can be configured to require approval for grant requests.
-
No approval: Access is granted automatically upon request (for lower-risk operations).
-
Approval required: Designated approvers must explicitly approve the request (for sensitive operations).
-
Approvers: If an approval workflow is enabled, the entitlement specifies the identities (Google Accounts, Google Groups, Google Workspace domains, Workforce pool identifiers) who are authorized to approve or deny grant requests.
-
Justification requirements: Entitlements can be configured to require a justification from the requester and/or the approver, promoting accountability and auditability.
-
Notification targets: You can configure additional email addresses to receive notifications about entitlement availability, pending approvals, and granted access.
Find the relevant entitlement for your request
Think of each entitlement as a "package" of permissions for a specific task or duration. To request access, you need to identify the most suitable package for your needs.
1. Identify Your Task/Role:
-
What specific privileged action do you need to perform? (e.g., "manage VM instances," "view sensitive BigQuery data," "administer a Cloud Storage bucket").
-
What IAM roles are typically associated with that task? (e.g., compute.admin, bigquery.dataViewer, storage.admin).
2. Search/Filter Entitlements:
-
Google Cloud Console:
-
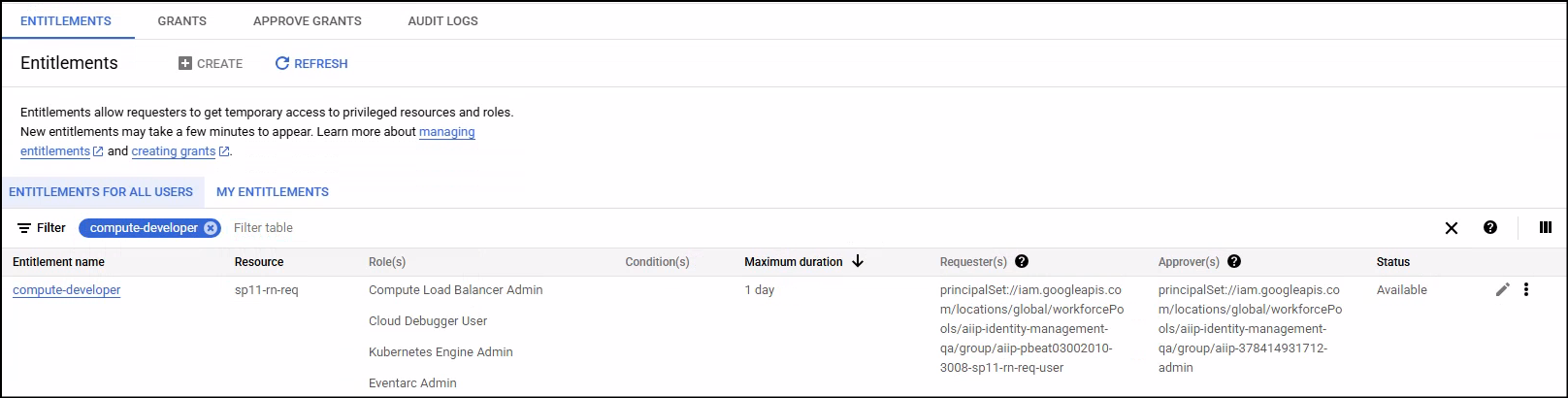
Use the search bar above the Entitlements for all users or the My entitlements tab to filter by Entitlement name. For example, typing "compute-developer" might show entitlements that grant this role.
-
Review the "Role(s)" column to see if any entitlement offers the specific IAM role(s) you require.
-
Check the "Max duration" and "Requires approval" columns to ensure the entitlement aligns with your operational needs and time constraints.
-
-
Choose the Best Fit:
-
Select the entitlement that grants the least privilege necessary for your task. Avoid requesting broad "admin" roles if a more specific role will suffice.
-
Consider the maximum duration – choose one that fits your expected work timeframe.
-
Be aware of approval requirements and internal processes for getting grants approved.
-
By following these steps, a user can efficiently navigate the PAM entitlements available in their GCP environment and request the specific access they need.